Secure Software Development
It is simply not enough to address security only at the end of the development lifecycle, for instance by commissioning pentests. There are a couple of reasons for that: (1) Costs for fixing a security issue are rapidly increasing the later it is done within an application lifecycle. (2) The architecture builds the fundament of a secure application. If an application is built upon an insecure fundament, it will never reach a really high level of security.
Therefore, security needs to be addressed throughout the whole software development lifecycle (SDLC). In this context, we often speak about building a Secure SDLC (SSDLC) or Secure Development Lifecycle (SDL), that integrates security practices (e.g. threat modeling, code review, SAST, pentesting, or application hardening) and security requirements into the software development process.
Such an SSDLC is, however, just one piece of a Secure Software Lifecycle Management (SSLM) that is visualized in the following diagram:
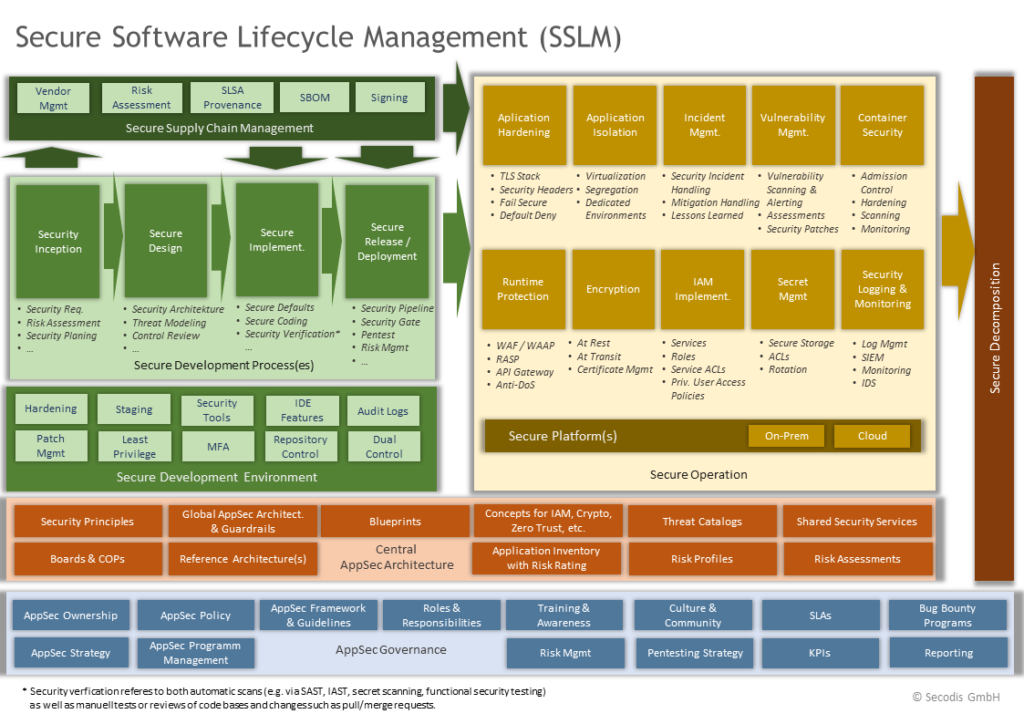
Implementation of an SSDLC or SSLM must take organization-specific aspects of software development (agile, non-agile), deployment, operation, and culture into account and can differ a lot from one organization to another.
We support you with all activities required to integrate application security into your development and procurement processes and to establish a working management system around it. The best approach for this is setting up an application (software) security program that is usually divided into three phases:
- Phase 1: As-Is Assessment & planing (study, 3 – 6 months)
- Phase 2: Implementation, quick wins & piloting (6 months – 1 year)
- Phase 3: Rollout (usually in different stages)
An as-is analysis is based on activities such as interviews, architectural reviews, threat and risk assessments as well as of course pentests. Focussing on quick wins at the start is really helpful in order to archive quick success. Have a look at our blog.
Based on the results of phase 1 and the identified security goals of your company, we then with actually establishing the SSDLC based on four workstreams:
- Requirements: Specifying new as well as adapting existing standards and guidelines.
- Processes: Establishing security gates within development and procurement processes as well as specifying required roles for that.
- Qualification: Training and coaching of developers and stakeholders.
- Tools: Selecting and integrating required tools automating security checks.
A crucial part of this project is of course the management of it. Our consultants are all working in this industry with many years of professional experience from a large number of customer projects.